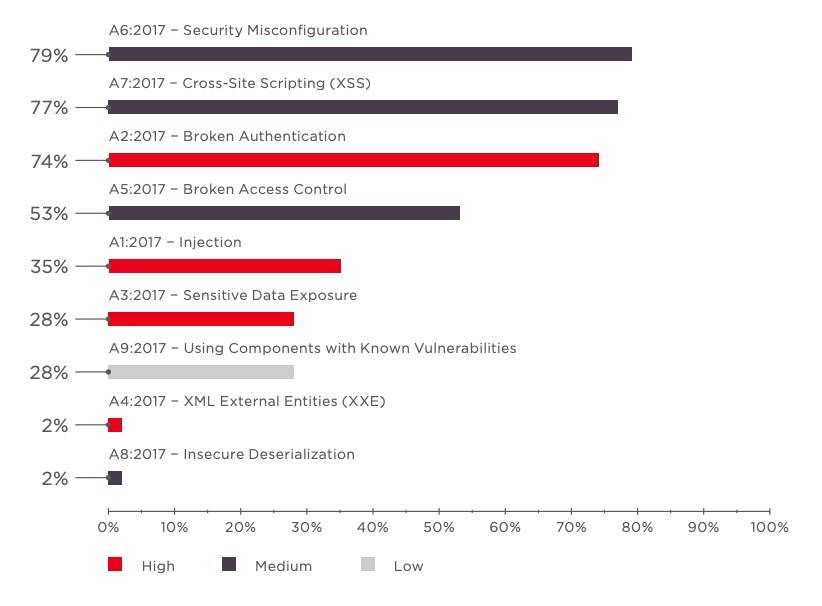
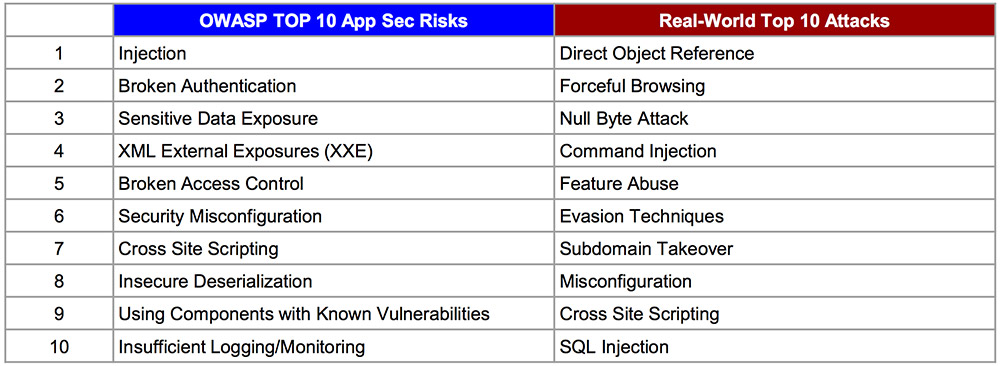
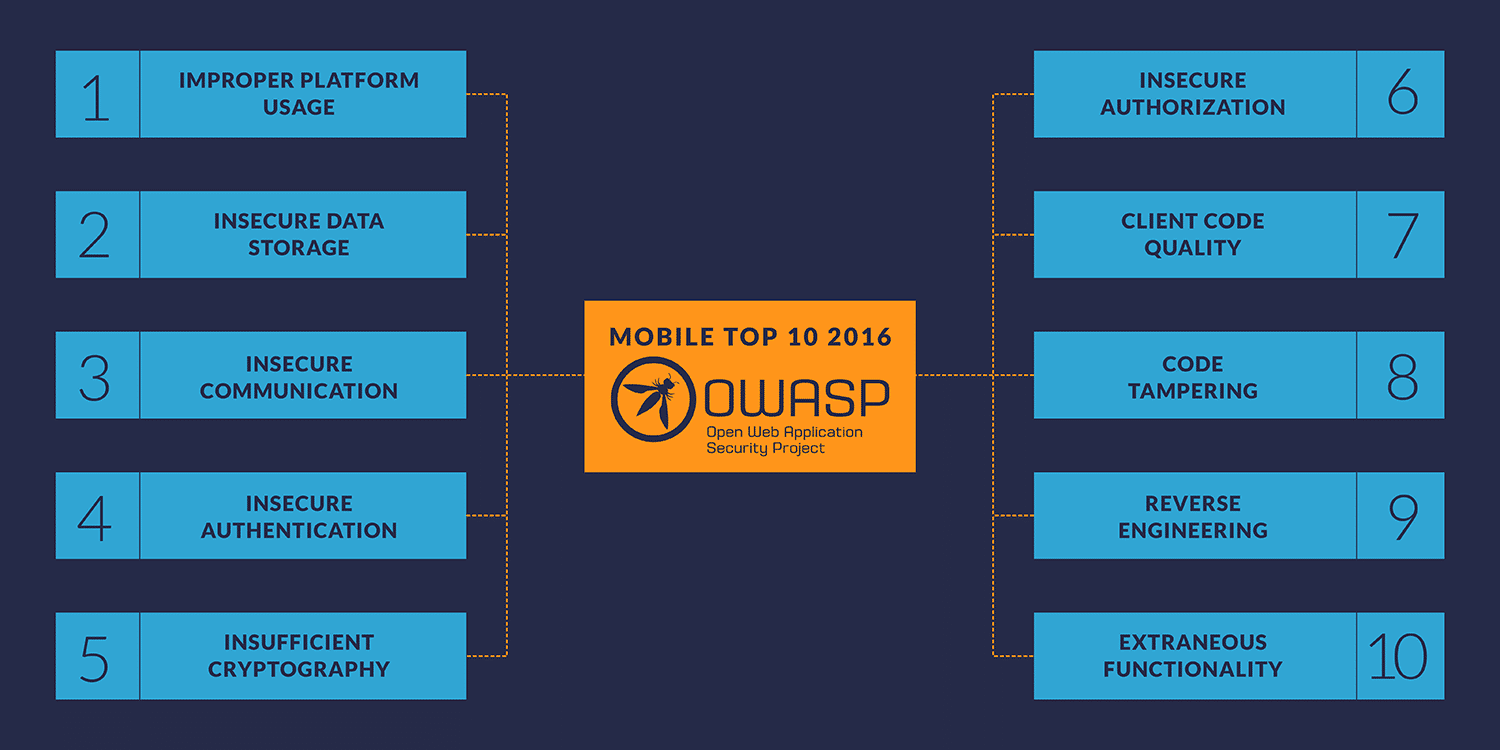
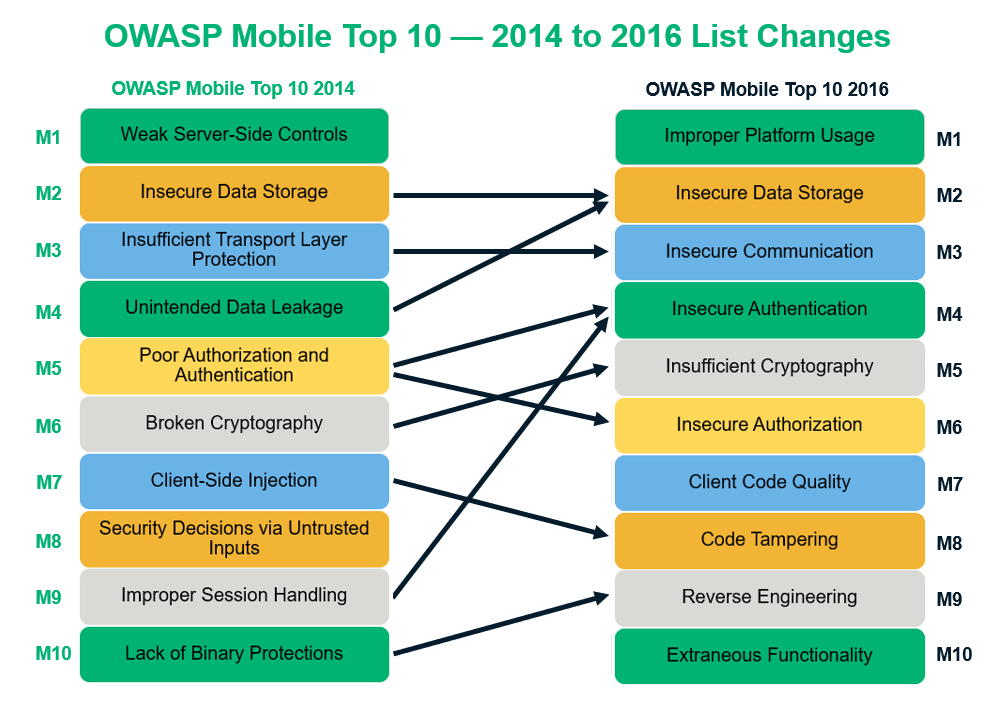
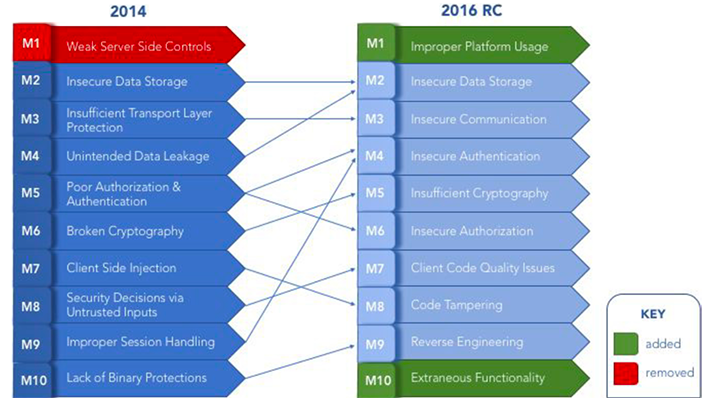
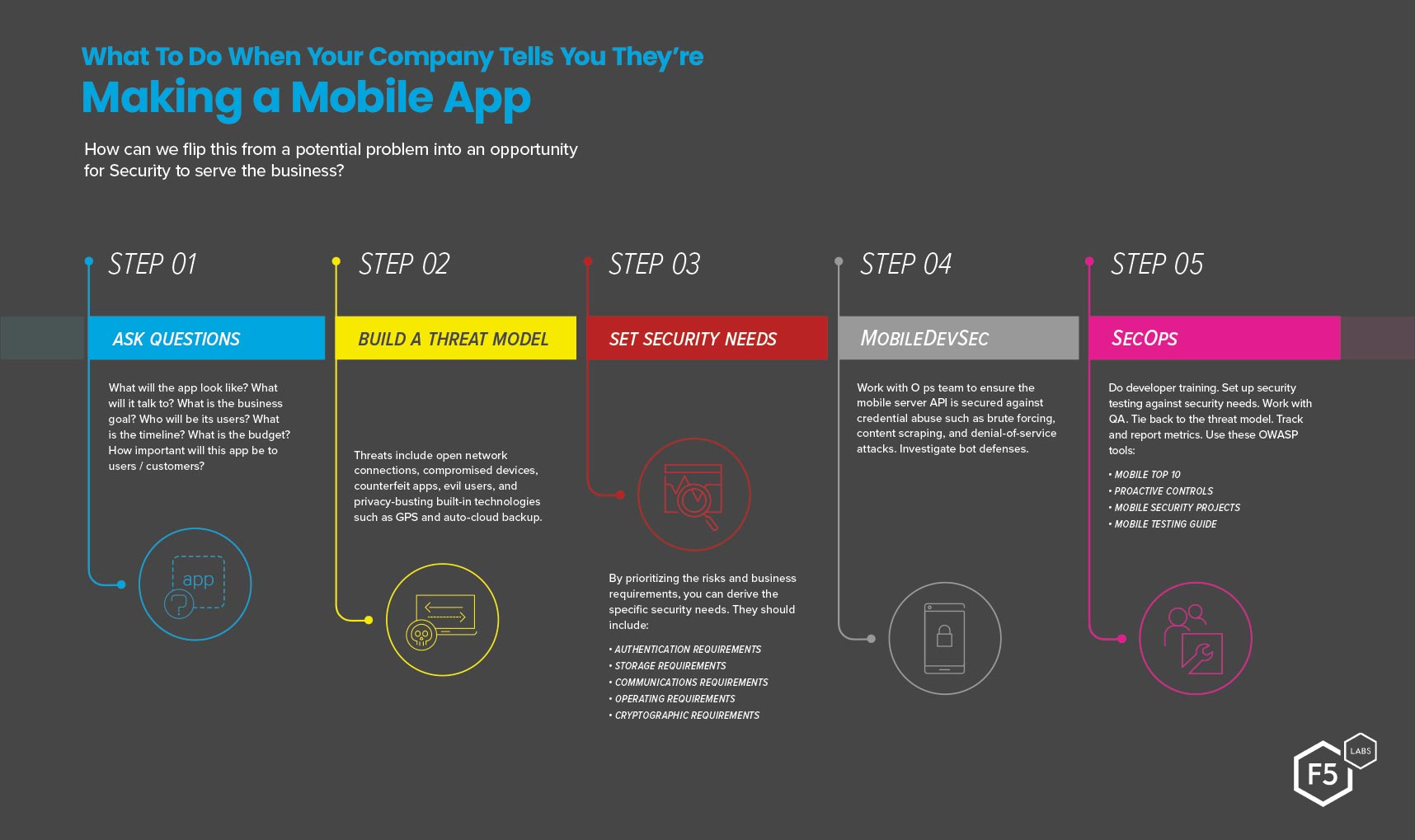
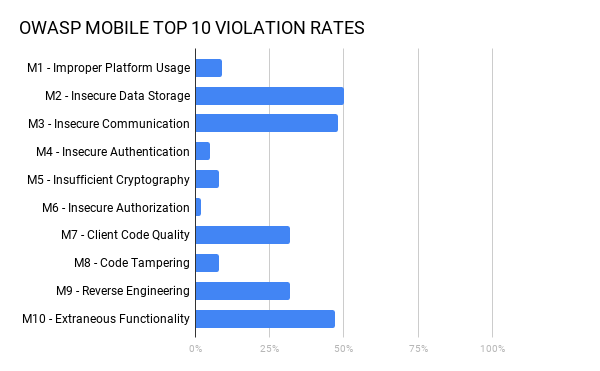
Mobile Applications Perform Poorly on Protecting Personal Data - Minimize the Attack Surface with Sentinel Mobile | NTT Application Security
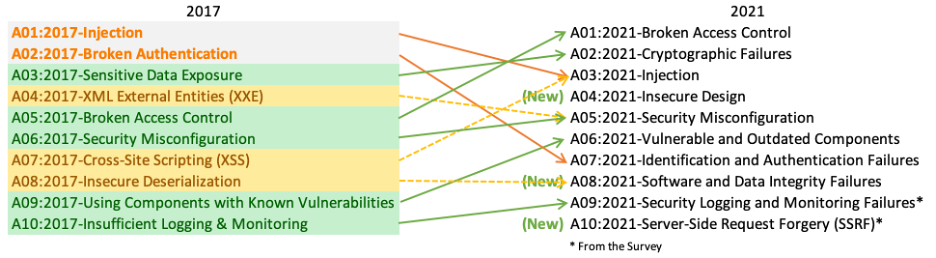
OWASP mobile top 10 security risks explained with real world examples | by Kristiina Rahkema | The Startup | Medium


![2021] OWASP Mobile Security Testing Top 10 Vulnerabilities Udemy Free Download 2021] OWASP Mobile Security Testing Top 10 Vulnerabilities Udemy Free Download](https://media.onlinecoursebay.com/2019/03/28190935/1983660_291c-750x405.jpg)